Vietnam Outsourcing Risk Management for Global Teams in 2026

Vietnam outsourcing risk management is no longer a side concern for global teams scaling fast. Data laws tighten, IP risks rise, and vendor mistakes cost more each year. In this guide, MOR Software explains how this approach works today, where risks hide, and how you can protect data, code, and delivery before problems surface.
Why Is Outsourcing Risk Management Important Today?
Outsourcing into Vietnam continues to grow as global teams scale faster and push more sensitive work offshore. The U.S. Department of Commerce cites a World Bank estimate that Vietnam’s digital economy will exceed USD 43 billion by 2025. This explains why more global work is landing there. With that growth comes tighter compliance pressure, higher data exposure, and greater reliance on vendors. This shift turns outsourcing risk management into a daily operational need, not a background concern.
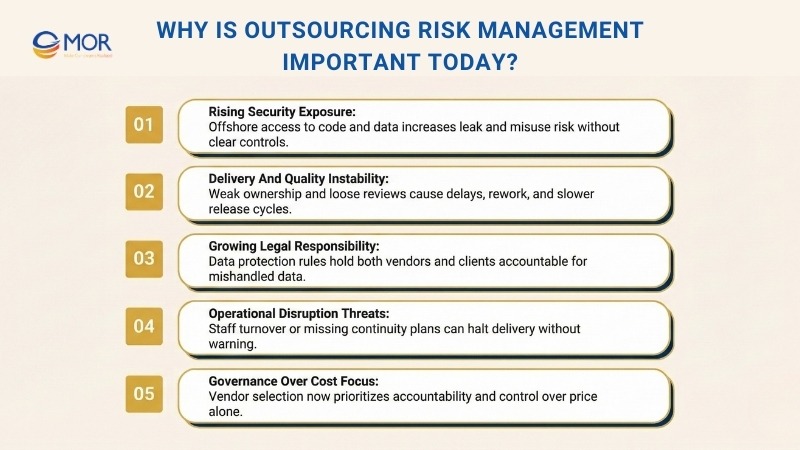
Why Is Outsourcing Risk Management Important Today?
- Rising security exposure: Offshore teams often access source code, internal systems, and personal data. With Vietnam’s Ministry of Information and Communications estimating 659,000 cyberattacks hit Vietnamese organizations in 2024, weak access rules or poor monitoring increase the chance of leaks and misuse. Many outsourcing risks begin with unclear controls, shared accounts, or missing activity logs.
- Delivery and quality instability: Delays often trace back to weak ownership and loose review processes in IT outsourcing risk management. Teams may work hard, yet output still drifts when roles stay vague. Over time, this leads to rework and slower release cycles.
- Growing legal responsibility: Vietnam’s data protection rules place obligations on both vendors and foreign clients. If a partner mishandles data, responsibility does not stop at the vendor. This reality pushes outsourced risk management higher on leadership agendas.
- Operational disruption threats: Staff turnover, vendor dependency, or missing backup plans can pause delivery without warning. The National Statistics Office reported 197.9 thousand enterprises withdrew from the market in 2024, up 14.7% year on year. Recovery takes longer when continuity planning is absent.
For example, a fast growing SaaS company expanded its Vietnam team and granted broad system access to speed delivery. One contractor left, but access was never revoked. The issue surfaced weeks later during an internal review, not after a breach, yet cleanup still took time and internal trust suffered.
Vendor selection now reflects these pressures. Cost and skills still matter, but governance and accountability matter more. A clear outsourcing risk management framework has become a baseline requirement for sustainable offshore partnerships.
Key Risks Businesses Face When Outsourcing to Vietnam
Outsourcing work to Vietnam opens real opportunities, but it also introduces new exposure points. When teams operate across borders, distance alone can hide weak controls. Most risks do not come from technical gaps. They come from governance gaps. That is why outsourcing risk management must start with a clear view of where things usually break.
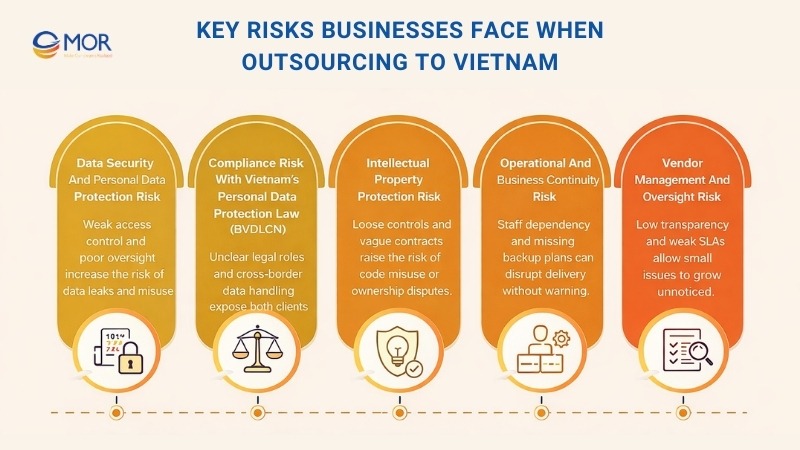
Key Risks Businesses Face When Outsourcing to Vietnam
Data Security and Personal Data Protection Risk
Data security sits at the center of most outsourcing concerns. Offshore teams often need access to source code, customer records, internal dashboards, or test databases. Once access expands, the surface area for mistakes grows.
In many outsourced risk management cases, data leaks happen through simple missteps. Shared accounts remain active. Access rights never get revoked. Logs exist but no one reviews them. Over time, these small oversights add up. One unsecured laptop or poorly configured cloud folder can expose sensitive data.
Personal data adds more pressure.The State Bank of Vietnam reporting 7 billion payment transactions in 2023, a 10 times increase compared with 2019, names, emails, IDs, and usage history move between systems daily. If vendors handle this data without strict rules, unauthorized access becomes hard to trace. This risk increases in third party outsourcing, where subcontractors or external tools also touch the data.
Supervision plays a major role here. When companies treat vendors as black boxes, visibility disappears. You may not know who accesses what, when, or why. In outsourcing risks tied to security, lack of oversight causes more damage than weak technology.
For instance, a project team granted temporary database access to an external tester during a release rush. The access stayed open after testing ended. Months later, an audit flagged unexpected login activity tied to that account. No breach occurred, but the cleanup required system reviews, access resets, and uncomfortable client conversations.
Clear access policies, logging, and review cycles form the backbone of outsourced risk manager solutions. Without them, even skilled teams create exposure without realizing it.
Compliance Risk with Vietnam’s Personal Data Protection Law (BVDLCN)
Legal risk has grown fast in recent years. Vietnam now enforces strict rules on how personal data gets collected, stored, transferred, and deleted. These rules apply to local vendors and foreign clients alike.
Many foreign companies struggle with role clarity. Under the law, you may act as a data controller, while your vendor acts as a processor. Each role carries specific duties. Consent management, purpose limitation, retention periods, and deletion rules must all align. When these details stay unclear, violations follow.
In risk management outsourcing scenarios, companies often assume vendors handle compliance alone. That assumption creates trouble. If a breach occurs, regulators look at both sides. Contracts, policies, and actual practices all come under review.
For example, a global platform allowed its Vietnam partner to process user profiles without clearly defining controller and processor roles. Consent records stayed fragmented across systems. During a compliance review, the company struggled to prove lawful data use, which led to rushed contract updates and delayed feature releases.
Cross border data transfer adds another layer. Moving Vietnamese personal data outside the country requires clear justification and safeguards. Without preparation, this step exposes you to penalties and operational delays.
That is why outsourcing risk management framework planning must include legal mapping from day one. Clear agreements, documented processes, and shared accountability reduce surprises later. In Vietnam, compliance risk no longer sits on the sidelines. It shapes how outsourcing relationships survive long term.
Intellectual Property Protection Risk
Intellectual property risk often worries decision makers the most. Your product logic, architecture, and source code represent years of investment. IP exposure rarely comes from outright theft. It usually comes from loose controls and unclear ownership.
- Uncontrolled source code access: When too many people can view or download code, misuse becomes easier. In outsourced risk management, access must stay limited and logged. Shared credentials or personal devices weaken protection fast.
- Weak contract language: Vague IP clauses leave room for dispute. If ownership, usage rights, and transfer terms stay unclear, enforcement becomes difficult. This risk shows up often in outsourcing vendor agreements that rely on generic templates.
- Reuse across projects: Developers may work on several products over time. Without isolation, code patterns or libraries can travel unintentionally. In outsourcing, this risk grows when subcontractors enter the picture.
- Lack of repository governance: Central repositories without review rules invite mistakes. Branch controls, approval flows, and audit trails play a key role in any solutions.
Strong IP protection relies on structure, not trust alone. Clear ownership terms, controlled environments, and visible oversight help protect your assets throughout the project lifecycle.
Operational and Business Continuity Risk
Operational risk often stays hidden until something breaks. Delivery may look stable, yet a single disruption can stall progress for weeks. In outsourcing risk management, continuity planning separates reliable partners from risky ones.
- Service interruption: Power issues, system outages, or network failures can stop work without warning. When vendors lack redundancy, recovery slows. This risk affects teams using software development outsourcing Vietnam models with single site delivery.
- Staff dependency: Projects may rely on a few key engineers. If one leaves or falls ill, progress pauses. Without cross training, knowledge gaps grow fast.
- Missing backup plans: Data backups, environment replicas, and failover systems matter. Many outsourcing risks trace back to vendors treating backups as optional rather than required.
- Limited incident response: When problems appear, response speed matters. Vendors without clear escalation paths lose time during critical moments.
Operational continuity depends on preparation. Vendors with documented plans, tested backups, and shared ownership help you stay in control when pressure rises.
Vendor Management and Oversight Risk
Vendor oversight risk often causes other problems to grow unnoticed. When visibility stays low, small issues turn into large ones. In Vietnam IT outsourcing, management gaps create long term exposure.
Lack of transparency sits at the top of the list. Some vendors keep internal workflows opaque. You may not see how tasks get assigned, reviewed, or approved. That limits your ability to spot delays or quality drift early.
Contract structure adds another layer. Without clear SLAs, expectations blur. Timelines slip. Responsibilities overlap. In risk management outsourcing, SLAs define accountability, not paperwork.
For instance, a product team relied on weekly status emails without access to task boards or review logs. Issues only surfaced after missed milestones. When the client asked for details, the vendor could not show who approved changes or why testing slipped. By the time gaps became visible, recovery required extra budget and reset timelines.
Audit access is also important. Vendors that resist audits raise red flags. Regular reviews, security checks, and delivery reports build confidence over time.
Effective outsourcing risk management depends on active governance. Clear communication, shared metrics, and audit rights keep partnerships healthy and predictable.
Vietnam’s Legal Framework for Outsourcing Risk Management
Vietnam’s legal environment around data and outsourcing has tightened in recent years. This shift directly affects how you plan outsourcing risk management when working with local vendors. Laws now place clear duties on both service providers and foreign clients. If you outsource work into Vietnam, legal awareness becomes part of daily operations, not a once-a-year review.
This framework is the most important for data handling, compliance accountability, and cross-border cooperation. Many outsourcing risks today come from legal blind spots rather than technical gaps.
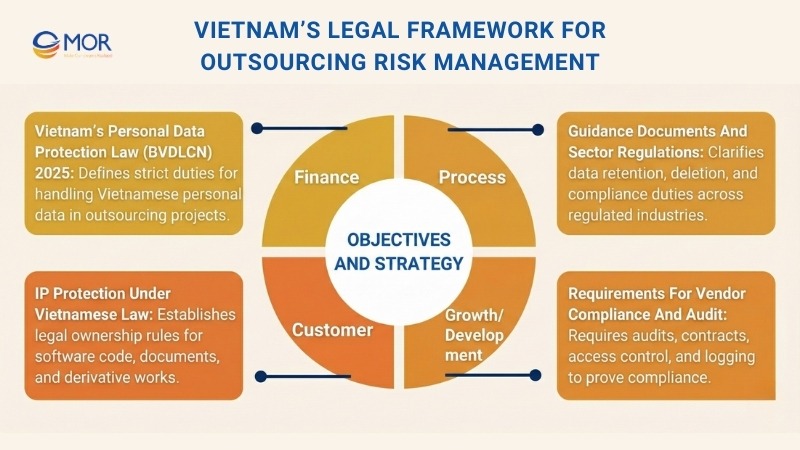
Vietnam’s Legal Framework for Outsourcing Risk Management
Vietnam’s Personal Data Protection Law (BVDLCN) 2025
Vietnam’s Personal Data Protection Law, often called BVDLCN, reshapes how personal data must be handled. It applies to local companies and foreign businesses that process Vietnamese personal data. In outsourced risk management, this law directly affects project scope, access rights, and vendor controls.
We’ll outline a simplified view of what is the most important.
Area | What the law requires | What it means for outsourcing |
| Scope | Covers any processing of Vietnamese personal data | Applies to offshore teams and outsource vendor partners |
| Data roles | Defines data controllers and data processors | Foreign clients keep legal duties, not only vendors |
| Consent | Requires lawful basis and clear consent | Projects must document approval before data use |
| Security | Demands technical and organizational safeguards | Access control and logs become mandatory |
| Penalties | Fines, suspension, or forced remediation | Weak compliance raises legal and financial risk |
For global teams, this creates new pressure points. If your Vietnam partner mishandles data, liability may extend back to you. That reality pushes outsourcing risk management framework planning earlier in vendor selection.
Guidance Documents and Sector Regulations
BVDLCN does not stand alone. Supporting guidance and sector rules clarify how companies should act in practice. These documents matter for IT outsourcing risk management, especially in finance, healthcare, and technology projects.
Regulators expect clear rules on data lifecycle management. That includes how long data stays stored, where it lives, and how it gets removed. Many outsourced risk management solutions now focus on retention schedules and deletion controls.
Data retention rules require teams to store personal data only as long as needed. Once the purpose ends, data must be removed or destroyed. This applies to production systems, test environments, and backups.
Deletion and destruction duties also receive more attention. Secure deletion, physical destruction of records, and proof logs help demonstrate compliance. Vendors that lack these processes increase outsourcing exposure.
For you, the takeaway stays simple. Legal compliance in Vietnam now ties directly to operational design. Vendors must show how they store, delete, and protect data. Without that clarity, outsourcing risk management stays incomplete.
IP Protection Under Vietnamese Law
Vietnamese law gives clear protection to software intellectual property. That protection applies to source code, architecture, documentation, and derivative works. In software outsourcing in Vietnam, IP ownership depends less on assumptions and more on contract clarity and execution discipline.
We walk you through a practical snapshot of how IP protection works in outsourced software projects.
Area | Legal expectation | What you should confirm |
| Ownership | IP belongs to the party defined in the contract | Contracts must state full ownership transfer |
| Scope | Covers source code, binaries, designs, and documents | No gaps between deliverables and ownership |
| Moral rights | Authors retain attribution rights under law | Waivers or usage rights should be addressed |
| Reuse limits | Vendors cannot reuse client IP without permission | Clauses must ban reuse across other projects |
| Enforcement | IP disputes rely on written agreements | Verbal understanding carries little weight |
For global teams, IP risk often grows during growth phases. New developers join. Repositories expand. Without written clarity, protection weakens. Strong management starts with legal precision before the first line of code is written.
Requirements for Vendor Compliance and Audit
Legal rules alone do not protect your project. Compliance must be visible and verifiable. In risk management outsourcing, audits and controls turn promises into proof.
- Periodic audits: Vendors should allow scheduled and ad hoc audits. These reviews check security controls, access records, and delivery practices. In Vietnam IT outsourcing, audit access signals maturity.
- Clear contractual documents: SLAs define delivery rules. NDAs protect confidential data. DPAs clarify data handling roles. Together, these documents anchor outsourced risk management in real obligations.
- Defined legal responsibilities: Contracts must state who acts as data controller and processor. This matters under Vietnamese law and affects liability exposure for foreign clients.
- Access control standards: Vendors should restrict system access by role. Shared accounts raise red flags. In third party outsourcing, access logs help trace activity when issues arise.
- Encryption and logging: Sensitive data should stay encrypted at rest and in transit. System logs must record access, changes, and deletion actions. These records support audits and incident reviews.
Compliance works best when it stays routine. Regular checks, shared documentation, and visible controls build trust over time.
How MOR Software Manages Outsourcing Risk for Global Clients
When you work with offshore teams, trust must be built into systems, not personalities. At MOR Software, we treat outsourcing risk management as an operational discipline that runs across legal, technical, and delivery teams. This approach helps global clients stay in control while scaling projects.
Our focus stays practical. Clear rules, visible controls, and shared accountability guide every project phase.
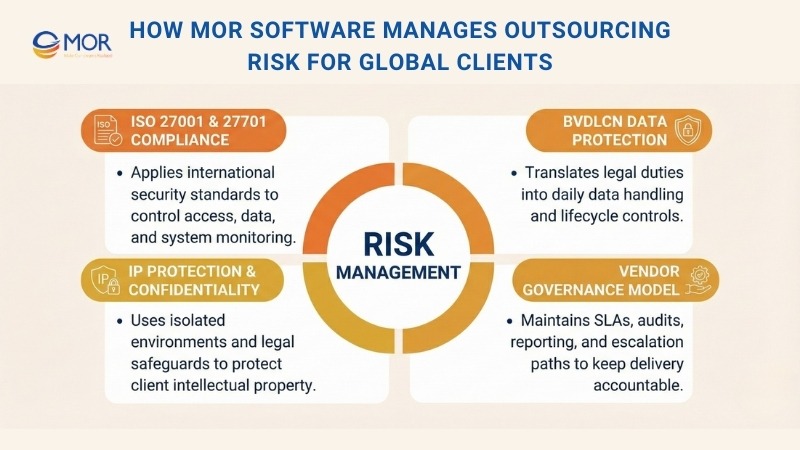
How MOR Software Manages Outsourcing Risk for Global Clients
Security Compliance Framework Based on ISO 27001 & 27701
Our security model follows ISO 27001 and ISO 27701 standards. These standards shape how we protect data, control access, and monitor activity across systems used in Vietnam IT outsourcing projects.
Internally, we define security ownership at every layer. Management sets policy direction. Technical teams apply controls. Audit teams verify compliance. This structure reduces ambiguity and keeps decisions consistent.
Access control stays strict. Every system uses role based permissions. Team members receive only what they need for their tasks. Shared accounts are not allowed. This approach supports IT outsourcing risk management by limiting exposure if credentials are compromised.
Activity logging plays an equal role. We record system access, code changes, and data handling actions. Logs stay protected and reviewable. When questions arise, evidence exists.
Security monitoring runs continuously. Alerts flag unusual behavior early. That allows teams to respond before issues spread. For global clients, this visibility adds confidence when working with offshore development Vietnam teams.
Data Protection Practices Aligned with Vietnam’s BVDLCN
Vietnam’s Personal Data Protection Law places clear duties on data handling. Our internal policy VS01-2026 translates those legal duties into daily actions. This keeps outsourced risk management aligned with local law and client expectations.
We apply data protection across the full data lifecycle.
- Controlled data collection: Personal data is collected only for defined purposes. Consent records stay documented. This supports compliance under risk management outsourcing models involving sensitive user data.
- Secure storage rules: Data stays in approved systems with access restrictions. Encryption applies to sensitive records. Backup systems follow the same controls as production environments.
- Defined retention periods: Each data type has a documented retention timeline. HR, finance, and project data follow legal and operational rules. Over retention increases risk and is avoided.
- Secure deletion and destruction: When data reaches end of purpose, it is deleted or destroyed using approved methods. Logs and records confirm completion.
- Incident response handling: Any suspected data issue triggers a formal response. IT, Legal, and operations coordinate actions and documentation. Transparency remains a priority.
Responsibility stays shared but defined. HR manages employee and candidate data. IT controls systems and access. Legal interprets regulatory duties. Project teams follow approved handling rules during delivery. This division prevents gaps that often appear in outsourcing risks scenarios.
Strong data protection depends on routine behavior. Policies alone do not protect data. Daily practice does. By aligning structure, tools, and accountability, we help clients manage risk without slowing delivery.
For global teams, this model creates balance. You gain scale and speed while maintaining control over data, compliance, and accountability.
Strong IP Protection and Confidential Development Environment
Protecting intellectual property requires more than contracts. It depends on how teams work each day. IP risk often appears when environments stay open and controls stay loose. We address this through structure and discipline.
Our development environments stay isolated by project. Each client receives a dedicated setup. Code, documents, and assets never mix across teams. This isolation limits exposure and supports long term outsourcing risk management goals.
Centralized repositories play a key role. All source code lives in managed version control systems. Direct copying to personal devices is restricted. Downloads stay monitored. These controls matter in outsourced risk management, where code reuse can happen unintentionally.
Legal protection strengthens technical controls. NDAs bind every team member. DPAs define how data and code are handled. Contracts clearly state IP ownership, usage limits, and transfer rights. In third party outsourcing, these documents reduce ambiguity and protect enforcement rights.
Together, environment control and legal structure reduce IP exposure. Trust becomes a result of design, not assumption.
Vendor Governance Model for Risk Reduction
Risk rarely comes from one failure. It grows when oversight weakens. A strong governance model keeps delivery predictable and accountable. In outsourcing risk management, governance connects strategy with daily execution.
- Clear SLAs: Service levels define timelines, quality benchmarks, and response expectations. When issues appear, SLAs provide a reference point. This clarity supports risk management outsourcing by setting shared rules from day one.
- Transparent progress reporting: Delivery updates stay regular and structured. Milestones, blockers, and changes are visible. This reduces surprises and supports informed decision making for outsourcing vendor relationships.
- Defined escalation paths: When risks surface, teams know who acts and how fast. Escalation avoids silence and delay, common drivers of outsourcing risks.
- Internal audits: Internal reviews check security, access, and process adherence. Findings lead to corrective actions, not blame.
- Customer side audits: Clients retain audit rights. Reviews may cover security, delivery, or compliance. This openness builds confidence in risk management solutions.
Governance works best when it feels routine. Clear rules, shared visibility, and regular checks keep projects stable. For you, this model turns outsourcing risk management into a steady process rather than a reaction to problems.
Best Practices for Outsourcing Risk Management in Vietnam
Strong results come from discipline, not hope. Risk rarely appears overnight. It builds quietly when ownership stays vague and rules stay loose. Good outsourcing risk management sets expectations early, then keeps them visible throughout delivery. When you treat risk as part of daily operations, teams act with more care and fewer surprises.
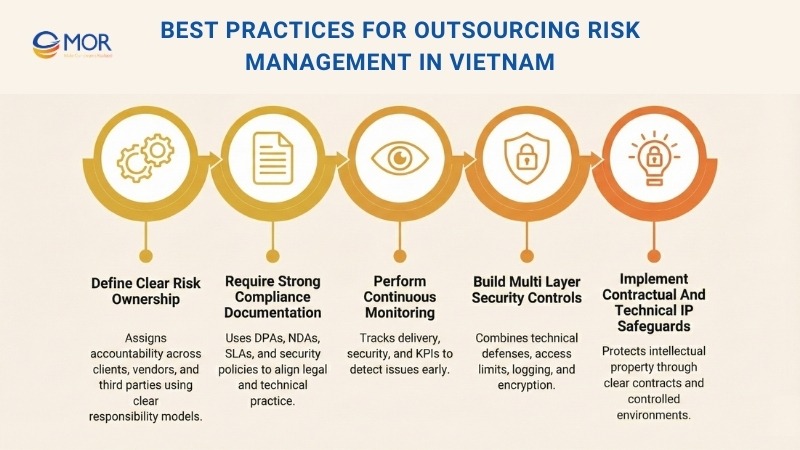
Best Practices for Outsourcing Risk Management in Vietnam
Define Clear Risk Ownership
Risk control fails when everyone assumes someone else is responsible. Clear ownership creates accountability across vendors, internal teams, and external partners. In Vietnam IT outsourcing, this clarity matters even more because work spans borders, time zones, and legal systems.
A simple RACI model keeps responsibility visible.
Activity | Client | Vendor | Third Party |
| Data protection compliance | Accountable | Responsible | Consulted |
| Security incident response | Accountable | Responsible | Informed |
| IP protection controls | Accountable | Responsible | Consulted |
| Regulatory reporting | Responsible | Consulted | Informed |
| Audit coordination | Accountable | Responsible | Consulted |
This structure supports outsourced risk management by removing guesswork. Each party knows where decisions sit and who must act. When an issue arises, response time improves and disputes drop.
Require Strong Compliance Documentation
Documents do not solve problems on their own. They set boundaries. In outsourcing risk management, strong documentation aligns legal intent with technical practice.
- Data Processing Agreement: A DPA defines how personal data is handled, stored, and removed. It clarifies controller and processor roles under Vietnamese law. This document matters in software development outsourcing Vietnam, where data often moves across systems.
- Non-Disclosure Agreement: NDAs protect source code, designs, and internal knowledge. Every team member signs before project access begins. NDAs limit downstream exposure in outsourcing.
- Service Level Agreement: SLAs define delivery scope, timelines, response times, and penalties. They support predictable outcomes and reduce friction with each outsourcing vendor.
- ISMS policies: Security policies outline access control, logging, and incident handling. They support audits and daily decision making in risk management outsourcing.
Documentation works when teams use it. Review these agreements during onboarding, not after a problem appears. When rules stay clear, outsourced risk management solutions feel natural rather than restrictive.
For businesses, these practices turn this management into a shared habit. That habit protects data, code, and delivery quality as projects scale.
Perform Continuous Monitoring
Risk control weakens when attention fades. In software outsourcing, monitoring keeps expectations aligned long after kickoff. It turns outsourcing risk management into an active process, not a checklist that gathers dust.
- Regular delivery reviews: Weekly or monthly reviews keep scope, quality, and timelines visible. You spot drift early and adjust before it grows into a dispute. This matters when working with any outsourcing vendor across borders.
- Security audits: Scheduled audits review access rights, data handling, and incident logs. These checks support third party outsourcing relationships where trust depends on verification.
- Technical KPI tracking: Metrics like defect rates, response times, and system uptime reveal delivery health. KPIs give you objective signals instead of gut feelings, a core part of outsourced risk management solutions.
Monitoring works when it stays routine. Small, steady checks prevent large, disruptive surprises later.
Build Multi-layer Security Controls
Security rarely fails in one place. It fails across gaps. In software development outsourcing Vietnam, layered controls close those gaps and limit blast radius when issues appear.
- Technical controls: Firewalls, endpoint protection, and secure repositories protect systems at the base level. These controls support outsourcing risk management through consistent defense.
- Access control: Role-based access limits who sees what. Teams receive only what they need to work. This approach reduces internal misuse, a common source of outsourcing risks.
- System logging: Logs record access, changes, and unusual activity. They support audits and incident response across Vietnam IT outsourcing projects.
- Encryption: Data stays encrypted at rest and in transit. Even if access occurs, readable data stays protected.
Layered security feels invisible when done right. Yet it quietly supports stability and trust.
Implement Contractual and Technical IP Safeguards
Intellectual property protection depends on clarity and control. IP risk often grows when contracts stay vague and environments stay open. Both need attention.
- IP ownership clauses: Contracts must state who owns code, designs, and derivatives. Ownership terms reduce conflict and support enforcement under outsourced risk management models.
- Controlled development environments: Isolated systems limit copying and reuse. Central repositories and monitored access protect assets across offshore development Vietnam teams.
Together, contracts and controls reinforce each other. Legal clarity sets rules. Technical safeguards enforce them. For you, this pairing keeps outsourcing risk management practical and dependable as projects scale.
Why Is Vietnam Still a Top Destination Despite These Risks?
Risk exists in every outsourcing market. What matters is how well those risks are understood and controlled. Many global teams accept the tradeoffs because the fundamentals stay strong. Cost, talent, and legal maturity continue to move in the right direction. When paired with solid outsourcing risk management, Vietnam remains a practical choice for long term delivery.
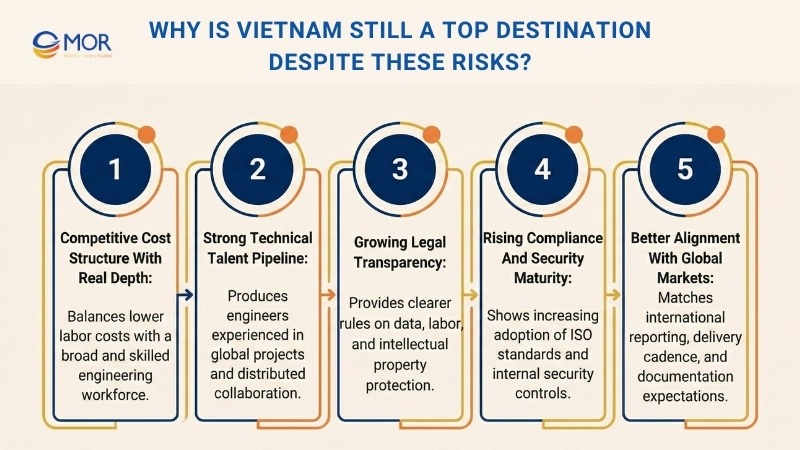
Why Is Vietnam Still a Top Destination Despite These Risks?
- Competitive cost structure with real depth: Labor costs remain lower than many regional peers. Yet savings alone do not explain the appeal. Vietnam offers a broad pool of engineers across web, mobile, cloud, and enterprise systems. This balance keeps software outsourcing costs Vietnam predictable while supporting complex work.
- Strong technical talent pipeline: Universities and private training programs continue to feed the market. Engineers gain early exposure to global projects. Many teams now work comfortably with distributed setups common in Vietnam IT outsourcing. Communication improves each year through daily collaboration with overseas clients.
- Growing legal transparency: Vietnam’s legal system now gives clearer guidance on data, labor, and intellectual property. Laws around personal data protection set expectations for both local and foreign firms. This clarity supports outsourced risk management by reducing guesswork in compliance planning.
- Rising compliance and security maturity: Vendors invest more in security controls, audits, and internal policies. Standards like ISO 27001 and ISO 27701 appear more often across Vietnam outsourcing companies. These efforts lower exposure tied to risks of outsourcing, especially in regulated industries.
- Better alignment with global markets: Many Vietnamese teams already serve clients in the US, EU, and Japan. They understand reporting standards, delivery cadence, and documentation needs. This alignment shortens onboarding for offshore development Vietnam projects.
Vietnam’s appeal does not come from ignoring risk. It comes from managing it. When vendors combine talent with structure, outsourcing risk management becomes part of daily work.
Build Your Outsourcing Strategy on a Strong Risk Management Foundation
Outsourcing brings speed and scale. It also brings exposure. That is why outsourcing risk management now sits at the center of every serious offshore plan. Security gaps, data misuse, IP loss, or weak oversight can undo months of progress in days.
When you choose vendors with mature compliance systems, risk drops fast. Clear controls, defined roles, and regular audits create stability. Data stays protected. Code stays owned. Teams stay focused on delivery instead of damage control. In long running programs, this structure often matters more than short term savings.
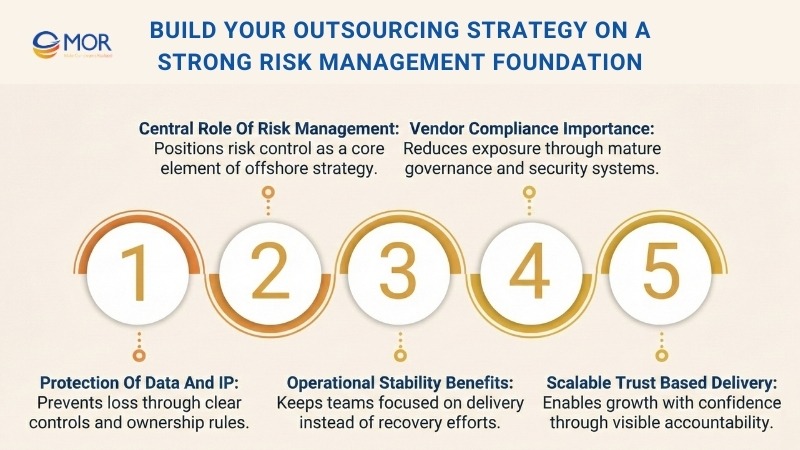
Build Your Outsourcing Strategy on a Strong Risk Management Foundation
We work with global clients who want confidence, not guesswork. Across projects, we support building governance into daily operations. Security reviews, data handling rules, IP controls, and audit readiness stay active from kickoff through delivery and support. That approach helps you scale safely, even as teams grow or scope changes.
A strong foundation does not slow work. It removes friction. With clear risk ownership and visible controls, decisions move faster and trust builds naturally.
Talk to MOR’s Security & Compliance Team
If you plan to expand or review outsourcing risk management in Vietnam, we can help. Contact us to discuss compliance, security controls, and practical risk planning for offshore teams.
Rate this article
0
over 5.0 based on 0 reviews
Your rating on this news:
Name
*Email
*Write your comment
*Send your comment
1