Blockchain Security: Key Risks And Protection Strategies
In today’s rapidly evolving digital landscape, blockchain has become a critical foundation for various industries. However, alongside potential come significant security challenges. So, how can your business ensure blockchain security for its systems? In this article, MOR Software will analyze common risks and share optimal implementation strategies for operational management for enterprises.
What Is Blockchain Security?
Blockchain security is a combination of technical measures, processes, and technologies designed to protect a blockchain network from potential threats. At its core, blockchain integrates cryptography, consensus mechanisms, and decentralized architecture to ensure that data and transactions cannot be forged, altered, or deleted.
Unlike traditional systems, blockchain does not rely on a single central server. Instead, information is stored and verified across a distributed network of nodes. This structure increases transparency, enhances tamper resistance, and minimizes the risks of blockchain security issues such as fraudulent transactions or data manipulation attacks.

What Is Blockchain Security?
Key Features Of Blockchain Security
Blockchain security has several key features that protect data and maintain network trust. These elements work together to ensure the system remains secure and operates reliably. Below are the essential components that form the foundation of blockchain security.
Decentralization
In blockchain security, decentralization is a foundational element that enhances the network’s defense. Instead of relying on a centralized server, which can easily become a single point of attack, blockchain distributes data and validation authority across thousands of nodes worldwide. This approach eliminates single points of failure, increasing uptime and resilience.
Moreover, decentralization increases transparency: every node holds a copy of the ledger, enabling public verification of transactions and minimizing the risk of fraud.
Cryptography
In blockchain security, cryptography is the core technology that ensures data integrity and confidentiality. The system uses asymmetric encryption and hashing algorithms to secure transaction information, allowing only authorized parties to decrypt the data.
The answer to how a hash helps secure blockchain technology lies in the fact that a hash converts input data into a fixed, irreversible string of characters. Any minor change to the data produces a completely different hash value, making tampering easily detectable. This is why an encrypted blockchain is both secure and trustworthy.
Consensus
Consensus mechanisms are essential to maintaining the integrity of the blockchain network without the need for a central authority. Protocols like Proof of Work (PoW), Proof of Stake (PoS), and Byzantine Fault Tolerance (BFT) allow nodes to agree on the validity of transactions.
For example, in the Bitcoin block, PoW ensures that only legitimate transactions are added to the blockchain, while preventing double-spending. This makes blockchain for security not just a concept, but a proven standard for securing decentralized transaction systems.
Immutability
Once data is recorded on the blockchain, it cannot be altered or deleted; this is the principle of immutability. Each block is linked to the previous one through cryptographic hashes, creating a continuous and unchangeable chain.
This property prevents major blockchain security issues such as transaction history manipulation or fraudulent record changes. In the case of block currency, immutability guarantees that all transactions are permanently transparent, strengthening user trust in the system.
Key Features Of Blockchain Security
Types Of Blockchain Security
The types of blockchain security are classified based on the access control model and the level of network protection. Each blockchain type has its own characteristics, directly influencing how blockchain and security are implemented in practice.
Public Blockchains (Permissionless)
A public blockchain is an open network that allows anyone to read, write, or validate transactions without permission. This model is the foundation of many blockchain and security applications, most famously the Bitcoin block and Ethereum.
The strength of public blockchains lies in transparency and resistance to censorship. All transactions are recorded on a distributed ledger, ensuring that any changes can be verified by the entire community. This reduces the risk of data tampering or fraudulent activity.
Private Blockchains (Permissioned)
A private blockchain restricts access, allowing only authorized entities to participate in transaction validation and network management. This model is often used by enterprises, where tailored blockchain security services are critical to meet high security requirements.
While centralized control minimizes external blockchain risks, strong internal security defenses are required to protect against insider threats. 76% of organizations have observed a continuous increase in insider attacks from 2019 to 2024, while only 29% believe they are adequately equipped with the necessary tools to prevent them.
Consortium Blockchains
A consortium blockchain blends the security of a private blockchain with distributed authority among multiple trusted organizations. A group of pre-selected participants jointly manages the network, validates transactions, and maintains data integrity.
This model is particularly effective for industry alliances where cybersecurity and blockchain work hand in hand to safeguard the system from cyberattacks and data breaches. However, shared governance introduces blockchain risks related to coordination and policy alignment, making a robust consensus mechanism essential.
Hybrid Blockchains
A hybrid blockchain combines elements of public and private blockchains, allowing certain data to remain publicly transparent while sensitive information is kept in a controlled, private environment. This structure is ideal for organizations that need a balance between open access and strict control.
To effectively secure blockchain operations, hybrid blockchains often utilize advanced encrypted blockchain technologies. These ensure that confidential data remains protected, while public-facing components retain transparency.
Types Of Blockchain Security
Key Enterprise Blockchain Security Components
Enterprise blockchain security components play a critical role in ensuring the safety and stability of the system. Below are the key components that enhance blockchain security in enterprise environments:
Identity and Access Management (IAM)
In enterprise blockchain systems, Identity and Access Management (IAM) defines how participants are authenticated and what permissions they are granted. By applying role-based access control, each user or node only has access to the functions and data relevant to their role.
IAM is particularly important in permissioned networks, where maintaining strict governance is essential for operational security.
Key Management
In blockchain security, key management plays a critical role in protecting cryptographic keys, essential elements for signing and validating transactions. Enterprises use secure methods like Hardware Security Modules (HSMs), cold wallets, and multisignature setups to reduce blockchain risks from stolen or lost keys.
An effective key management system ensures the integrity and security of all data within the blockchain network.
Data Privacy
Data privacy is an essential component of blockchain and security for enterprises. By implementing encryption and strict access control mechanisms, sensitive data is safeguarded from leaks or breaches.
This approach helps organizations comply with regulations such as GDPR or HIPAA while mitigating blockchain security issues related to unauthorized data exposure.
Secure Communication
Secure communication ensures that data exchanged between blockchain nodes is encrypted and protected. Implementing strong encryption protocols prevents man-in-the-middle attacks and reduces the risk of eavesdropping or tampering with messages.
Smart Contract Security
Smart contract security is critical to ensuring that the contract code is free from vulnerabilities before deployment. Enterprises typically conduct thorough audits to verify logic, structure, and potential exploits.
According to Beosin’s 2023 report, of the $1.397 billion stolen in blockchain incidents, more than 51.8% of attacks (99 out of 191 cases) originated from smart contract vulnerabilities.
This highlights the necessity of implementing regular security audits and adhering to secure coding standards to minimize risks and protect enterprise digital assets.
Transaction Endorsement
In permissioned and consortium blockchains, transaction endorsement requires specific authorized members to review and approve transactions before they are added to the ledger. This multi-party verification prevents unauthorized actions and ensures that all operations comply with the network’s governance rules.
Key Enterprise Blockchain Security Components
Common Blockchain Security Threats
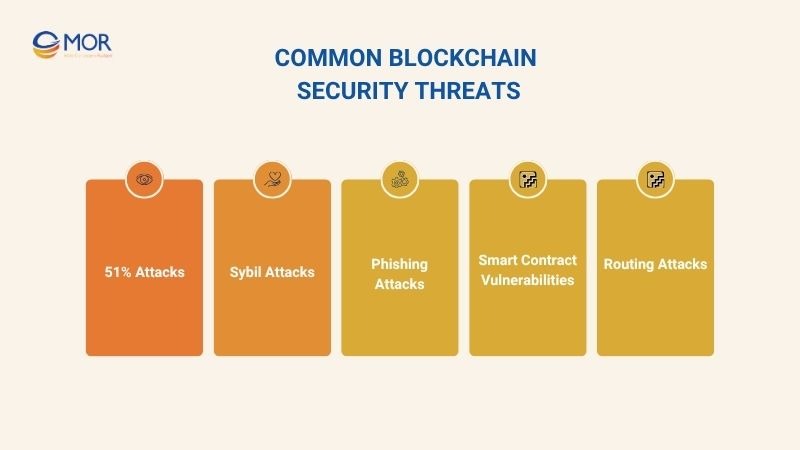
Common blockchain security threats are risks that can undermine the integrity and safety of the network. Early identification and a clear understanding of these risks are essential steps in securing blockchain and implementing the right blockchain security services to ensure long-term network protection.
51% Attacks
In blockchain security, a 51% attack is a serious threat to public blockchains. When a group or entity controls more than 50% of the mining power (hash power), they can reverse transactions, perform double-spending, and interfere with network operations.
A typical case is Bitcoin Gold, which allows the attacker to steal approximately $72,000 worth of BTG.
Sybil Attacks
In blockchain security, a Sybil attack occurs when the attacker creates multiple fake nodes to control or disrupt the network. This can weaken the consensus mechanism, affect transparency, and reduce system performance.
To secure the blockchain, prevention measures include node identity verification, access restrictions, and using dedicated blockchain security services.
Phishing Attacks
Phishing and private key leaks are major causes of asset losses. According to CertiK’s Q3 2024 report, over $750 million was stolen due to phishing and private key leaks in more than 150 incidents.
To reduce this risk, enterprises should use multi-factor authentication (MFA), perform regular threat monitoring, and train users to detect phishing scams.
Smart Contract Vulnerabilities
Vulnerabilities in smart contracts are a common cause of blockchain security issues. The Hack3d – CertiK report shows that in 2023, total losses from Web3 reached $1.84 billion from 751 incidents, with logic errors and exploits in smart contracts being frequent causes.
To secure the blockchain, it is essential to perform source code audits and apply secure development standards.
Routing Attacks
Routing attacks target the communication layer of the blockchain, where data is transmitted between nodes. Attackers can intercept or reroute data, causing delays or altering information.
Encrypting connections and implementing secure communication protocols are necessary to ensure blockchain security.
Common Blockchain Security Threats
Effective Blockchain Security Solutions
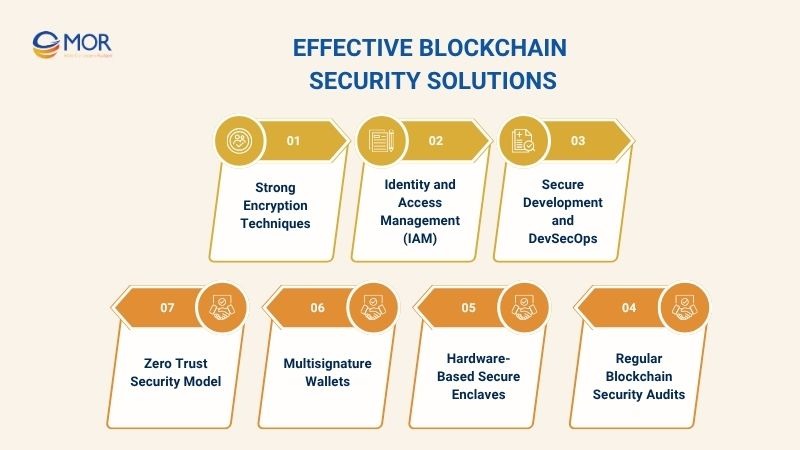
Effective blockchain security solutions play a critical role in protecting networks against potential threats. These measures form the foundation for strengthening defenses, ensuring data integrity, and maintaining system stability.
Strong Encryption Techniques
In blockchain security, encryption techniques form the foundation for protecting data and transactions against theft or tampering. Advanced blockchain networks typically use AES-256 to encrypt stored data and Elliptic Curve Cryptography (ECC) to secure private keys and verify digital signatures.
Real-world example: A cryptocurrency exchange was attacked by hackers who stole over $200 million worth of digital assets. However, most of the assets in cold wallets were encrypted with AES-256, and the private keys were secured with ECC, making decryption impossible for the attackers.
Identity and Access Management (IAM)
IAM plays a crucial role in blockchain security by ensuring that only authorized users and nodes have access. Applying the Principle of Least Privilege helps prevent unauthorized access and reduces the risk of privilege abuse.
Real-world example: An enterprise blockchain system implemented strict access control: administrators could configure the network, validator nodes could only approve transactions, and end users could only submit transactions. This hierarchical permission model significantly reduced the risk of internal data leaks.
Secure Development and DevSecOps
Implementing DevSecOps helps detect and address security vulnerabilities early in the development process. This includes adhering to secure coding standards, automated vulnerability scanning, and source code review before deployment.
Real-world example: A blockchain-based e-commerce platform used automated security checks for its smart contracts, identifying a logic flaw before release. This measure prevented a vulnerability that could have caused millions of dollars in losses.
Regular Blockchain Security Audits
In blockchain security, regular security audits are a proactive measure to detect and address vulnerabilities before they can be exploited. The process typically involves penetration testing, source code review, and evaluation of blockchain network infrastructure.
Real-world example: A DeFi platform conducting quarterly security audits discovered a reentrancy vulnerability in its staking smart contract. The flaw could have allowed hackers to withdraw assets multiple times within a single transaction. Early detection and remediation before deployment prevented potential losses of tens of millions of dollars.
Hardware-Based Secure Enclaves
A secure enclave is a blockchain security solution that uses an isolated execution environment to protect sensitive operations. Even if the operating system or software is compromised, data within the enclave remains secure due to physical isolation and hardware-based encryption mechanisms.
Real-world example: A digital asset custody provider deployed secure enclaves for multi-level transaction signing. During a server attack, the private keys stored in the enclave remained uncompromised, protecting all customer assets and preserving service credibility.
Multisignature Wallets
A multisig wallet is a blockchain security solution that requires multiple parties to approve a transaction. Typically, a multisig setup follows an M-of-N configuration, meaning M signatures are required out of N authorized signers.
Real-world example: A blockchain investment fund used a 3-of-5 multisig model for all custodian wallet transactions. When one member’s account was compromised, the hacker could not complete a withdrawal without the remaining signatures, protecting tens of millions of dollars in fund assets.
Zero Trust Security Model
Zero Trust is a blockchain security strategy based on the principle of “never trust, always verify.” This model requires continuous verification of identity, device, and activity for every node and user, along with monitoring of data traffic between network components.
Real-world example: A blockchain network in the financial sector implemented Zero Trust to monitor participating nodes. In one incident, the system detected a rogue node exhibiting abnormal behavior and immediately isolated it from the network, preventing a potential Sybil attack and ensuring data integrity.
Effective Blockchain Security Solutions
Best Practices For Blockchain Security
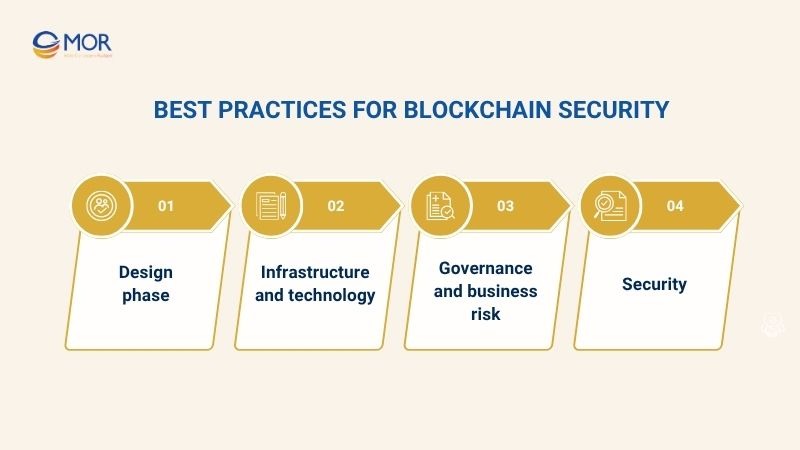
When developing a blockchain solution, the design phase plays a critical role in ensuring system security and stability. At this stage, organizations should address key considerations:
- What governance model will be applied for participating organizations or members?
- What type of data will be stored in each block, and how will sensitive data be protected?
- How will relevant regulatory requirements be met across jurisdictions?
- How will identity details and cryptographic keys be managed? What is the process for key rotation or revocation?
- What disaster recovery strategy will be in place for all blockchain participants?
- What are the minimum security requirements for blockchain nodes or clients?
- How will potential blockchain block collisions or conflicts be resolved?
For infrastructure and technology, a secure and resilient architecture is essential. Weak technology choices or poor infrastructure design can introduce vulnerabilities, increasing the risk of security breaches and data loss.
In terms of governance and business risk, enterprises must identify potential business risks, such as financial loss, reputational damage, and compliance violations. Governance risks, inherent to blockchain’s decentralized structure, require strict enforcement of decision-making criteria, governance policies, and robust Identity and Access Management (IAM) controls.
Regarding security, protecting a blockchain network involves identifying and managing all potential risks. Administrators should build a security framework that includes both a comprehensive risk model and a threat model. These models guide the implementation of effective security measures, ensuring that the blockchain ecosystem remains protected against a wide range of attack scenarios.
Best Practices For Blockchain Security
Why Choose MOR Software For Blockchain Security Solutions
MOR Software is a strategic partner, supporting businesses in building a comprehensive and sustainable blockchain security system. MOR’s strength lies in the combination of deep technological expertise and a clear understanding of each industry’s unique business context.
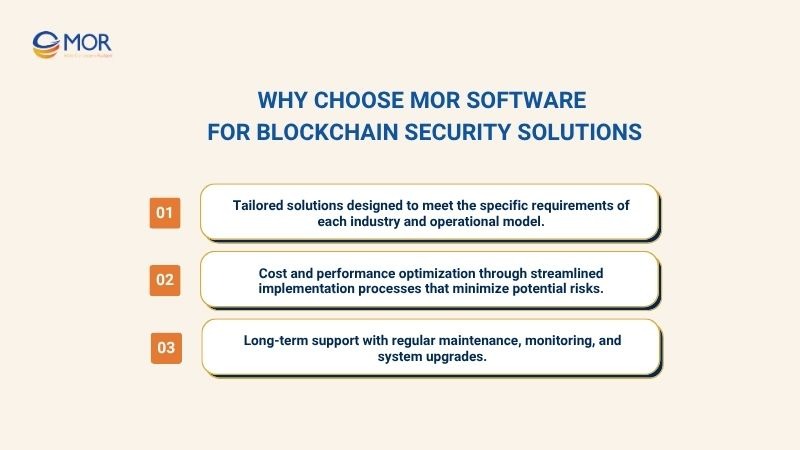
Our focus includes:
- Tailored solutions designed to meet the specific requirements of each industry and operational model.
- Cost and performance optimization through streamlined implementation processes that minimize potential risks.
- Long-term support with regular maintenance, monitoring, and system upgrades.
With extensive implementation experience and a flexible delivery approach, MOR Software is the strategic choice for businesses aiming to protect their blockchain systems and strengthen trust among customers, partners, and investors.
Why Choose MOR Software For Blockchain Security Solutions
In Conclusion
In the digital era, blockchain security has become a cornerstone for ensuring the stability and sustainable growth of enterprises. A secure blockchain system prevents attacks and strengthens trust among customers, partners, and investors. If your business is seeking a partner to protect digital assets, contact MOR Software today for a detailed consultation and the most suitable blockchain security solutions.
Rate this article
0
over 5.0 based on 0 reviews
Your rating on this news:
Name
*Email
*Write your comment
*Send your comment
1