What Is a Hash Function in Cryptography? The Ultimate Guide

A hash function in cryptography plays a key role in keeping data safe, yet many people still misunderstand how it works or why it matters. Questions about hash functions in cryptography often appear when teams try to protect systems or verify sensitive information. This MOR Software’s guide will walk you through the essentials so you can make smarter security decisions.
What Is Hash Function In Cryptography?
A phrase like hash function in cryptography can sound technical at first, yet the idea is quite clear once you look closer. When people talk about hash functions in cryptography, they usually refer to a method that creates a special value for any piece of data. In simple terms, it is a process that takes text of any size and turns it into a fixed string that works like a unique label.
Today, this simple method is important more than ever. Statista reports that known data breaches in the United States grew from 447 in 2012 to more than 3,200 in 2023. This idea means every input has its own result. When the content changes, the result changes too. It helps you check that data stays the same from the moment you send it until it reaches the other side, safe and untouched.
Some people mix this method with encryption, but they are not the same. Encryption hides data so someone can read it later with a key. Hashing does not work like that at all. A hash is not something you can reverse or unlock. To see why, IBM explains that breaking a strong 256 bit cryptographic key by brute force would take about 3.31 x 10^56 years, while the universe is only around 13.7 billion years old. This makes a well designed hash function feel like a one way street in real life. If someone talks about cracking or opening a hash, it shows they misunderstand how the process works.
We will look at the difference between these two topics later. For now, let us stay with hashing and how it looks in practice.
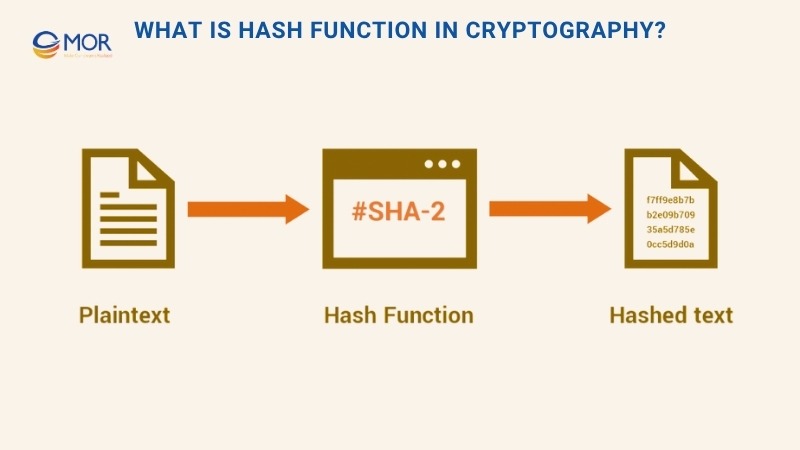
This picture shows how an input moves through a math formula and becomes an unreadable output. It looks simple at the top level, but there is a lot happening inside the function.
So how can we explain this idea in a more technical way? In short, hash functions cryptography comes down to a one-way method that turns any input into a fixed-length output. This output is called a digest, a value, or a code. It acts as the special identifier you learned about earlier.
When data moves through this process, the digest is usually smaller than the original message. Passwords are often an exception. It does not matter if the input is one line or a very long file. The output still has the same length. This stops others from learning anything about the size of the original content. That is important because Cybernews researchers, in a report covered by the Associated Press, recently found 30 exposed datasets that together hold 16 billion compromised credentials. Strong hashing is one of the last shields when that kind of login data leaks.
People mainly use this method for checking identity and keeping data safe. It also supports other tasks across many systems.
Can A Hash Function In Cryptography Be Reversed?
The answer is not as simple as it may seem. When people talk about a hash function cryptography process, they often describe it as a one-way method. This idea comes from the huge amount of power, time, and cost needed to test every possible input that could match a final digest. In theory, someone with endless resources could try to brute force it, yet that situation does not match real life.
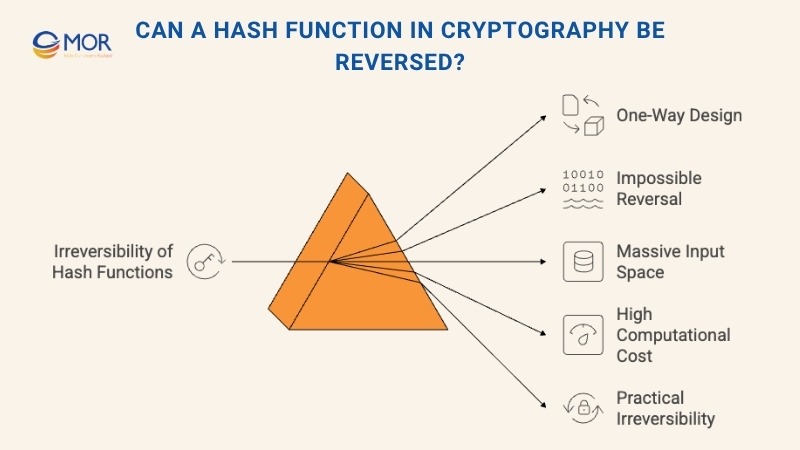
In practice, checking every possible value that leads to one digest is not realistic. The number of options is far too large. That is why specialists treat this method as an irreversible one-way path. It means the output cannot be turned back into the original data, and this rule is what keeps the method safe for modern systems.
Properties Of A Secure Hash Function In Cryptography
So, what makes a strong method for protecting data? A good design has several traits that help it work in a safe and predictable way. These traits also reflect how the properties of hash function in cryptography are used in real systems.
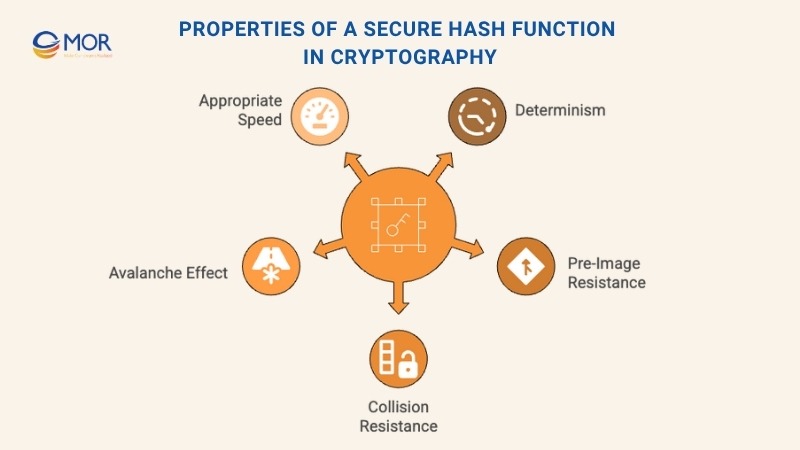
- Determinism. A reliable method must always return an output with the same length, no matter how large or small the input is. This means a short line and a long document still create results with equal size. It helps systems process information in a clear and steady manner.
- Pre-image resistance. This idea means it should be extremely hard to take an output and guess the original message. Since the method works only in one direction, there is no way to reverse it or recover the initial input. This is why the process is seen as a one-way path that protects sensitive information.
- Collision resistance. A collision happens when two different inputs create the same output. In cryptography, this is a serious problem because it means the method you are using is no longer safe. An attacker could make a harmful file that uses a fake result matching a trusted file and then pretend it is real. If this happens, the system cannot tell the difference. A trustworthy design must prevent this issue so every input always produces a unique result.
- Avalanche effect. This idea means that even a tiny change in the input, like adding one small character, causes a large change in the final output. A simple edit turns into a result that looks nothing like the original. This strong reaction is what people call the avalanche effect and it helps protect patterns inside the data.
- Hash speed. A secure method should work at a speed that fits its purpose. In many cases, people want a fast process because quick results help systems run smoothly. Still, this idea depends on how the method is used. A fast option works well for website activity and everyday checks. A slower option is better for password storage because extra time makes attacks harder. The right speed always depends on the task and the level of safety the system needs.
What Does A Hash Function In Cryptography Do?
One main purpose of a hash function in cryptography is to take readable data and create a fixed-size value that cannot be turned back into the original message. Still, this method does much more than that. When viewed from a wider angle, cryptography hash function also relates to several important tasks that help keep information safe. Strong designs can:
- Ensure data stays correct and unchanged,
- Prevent hidden edits or harmful changes,
- Protect stored passwords from attackers, and
- Work at different speeds so each system can choose the right option for its needs.
Ensuring Data Integrity
A hash function in cryptography helps check data integrity inside many secure systems. In simple terms, it works like a checksum that shows whether information has changed after it was signed. It also helps confirm the identity of the sender, since the value comes from the original message.
Imagine you connect to public Wi-Fi and send an email. This type of network is not safe at all. You write your message, sign it with your digital certificate, and send it across the internet. This situation is perfect for a man in the middle because someone on the same network can intercept the message and change it to suit their own goals.
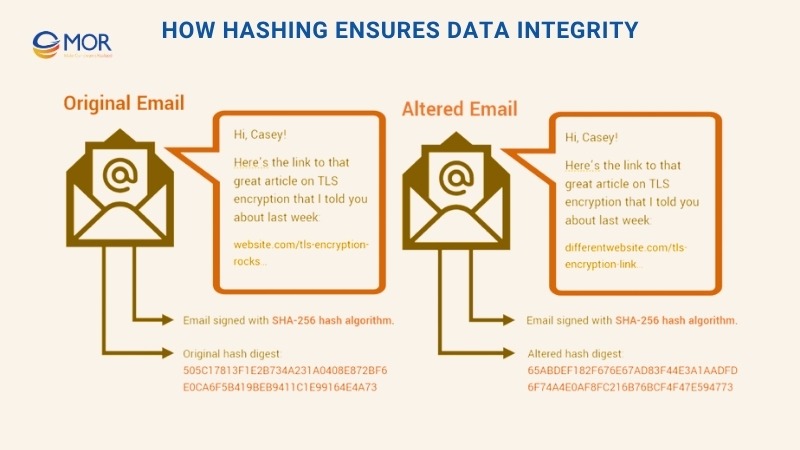
In the example above, a signed email is changed during transit. When even a small part of the message is modified after signing, the hash digest becomes completely different. This change tells you the email cannot be trusted.
When the message reaches me, I want to check if it is real. I can take the value attached to your signature and use the same method it mentions to create my own version. If my result matches the value you sent, the message stayed the same. If it does not match, then something is wrong and I know not to trust it.
Even tiny edits change the final result. A capital letter, a swapped symbol, or a small punctuation change will create a completely new value. This reaction is expected. Any difference in the result shows that the message is no longer the original one.
Detecting Unauthorized Modifications
A hash function in cryptography is very useful for keeping data accurate, but placing a hash on a message does not stop someone from changing it. What it does provide is a clear warning for the person who receives the message. Even a very small edit will create a completely different value, which shows the content was changed somewhere along the way.
You can think of this method like a smoke alarm. A smoke alarm cannot stop a fire, but it can alert you when something is wrong. Hashing works the same way. It tells you that the message is no longer the original version, so you know not to trust it.
Protecting And Storing Passwords Safely
Today, many online services let you save passwords so you do not need to type them every time you log in. But saving plain passwords on a public server is risky because criminals could steal them. To avoid this, websites turn each password into a hash value and store that value instead of the real text.
Still, a simple hash is not enough to stay safe from some attacks, including brute force attempts. This is why the system adds something called a salt. A salt is a random number that is added to the password before hashing. It creates an extra layer of protection and helps stop attackers who try to use rainbow tables or other password cracking methods.
This process makes stored passwords much safer and helps keep user accounts protected.
Varying Speed For Different Use Cases
Hash methods do not all work the same way. Each one is designed for a specific role, and their speed plays a big part in how well they fit that role. Some work very fast while others take more time. This difference can help or harm security depending on how the method is used. For this reason, some designs are seen as secure for certain tasks while others are not.
A fast method works well when you need quick, smooth connections on a website. Speed helps create a better experience for users. On the other hand, storing customer passwords needs a slow method. A slower option forces attackers to spend much more time and power when they try to run a cracking attack. This extra effort makes things harder for them and helps keep your users safe.
Common Applications Of Hash Functions In Cryptography
So, where do you see these methods in action? They are all around you in the tools and platforms you use every day. The application of hash function in cryptography appears in tasks like signing software, checking digital signatures, and securing website connections in browsers on both computers and phones. They also help with indexing and finding items in large online databases. For example, hashing helps verify:
- Data blocks in cryptocurrencies and other blockchain systems.
- The integrity of software, emails, and important documents.
- Passwords that are stored as hash values instead of plaintext. A small extra step, such as adding a salt, is needed to make these stored values safer.
These methods also play a major role in public key systems. In many cases, hashing is part of the process used in:
- SSL or TLS certificates that protect websites,
- Code signing certificates used to verify software,
- Document signing certificates, and
- Email signing certificates for secure communication.
They support trust, identity, and data protection across many digital services you rely on each day.
How Does A Hash Function In Cryptography Work?
When this method runs, it takes data of any size and passes it through a math formula that creates a fixed-length result. This result cannot be reversed, and it stays the same length no matter how long the input is. This is where the idea of a cryptography hash function comes from, since it always produces a clear and steady output.
In many cases, the input is divided into blocks of equal size. If one block is too small, padding with 1s and 0s is added to make it match the required length. Each block then goes through the hashing algorithm, and the final value appears at the end. The hash function in cryptography diagram below shows this step in a simple way.
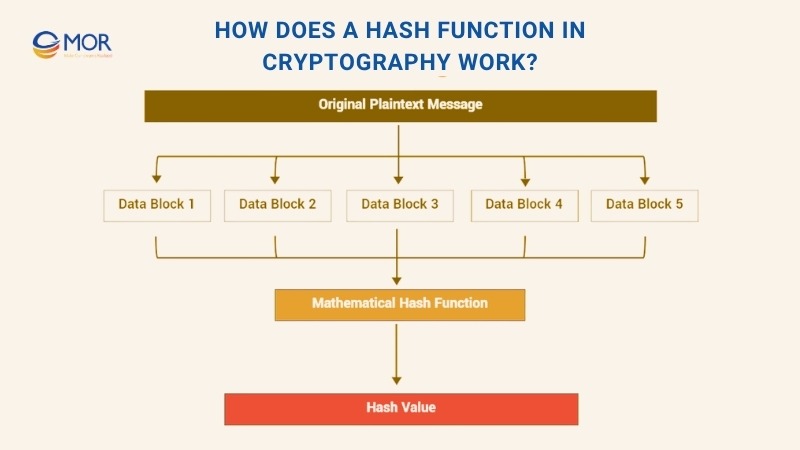
The steps can change when passwords are involved. For safe password storage, the system adds a salt before running the process. A salt is a unique and random value that changes the final result. Even one extra character creates a completely different output, which makes stored passwords much harder for attackers to guess.
Examples Of Hash Functions With Different Algorithms
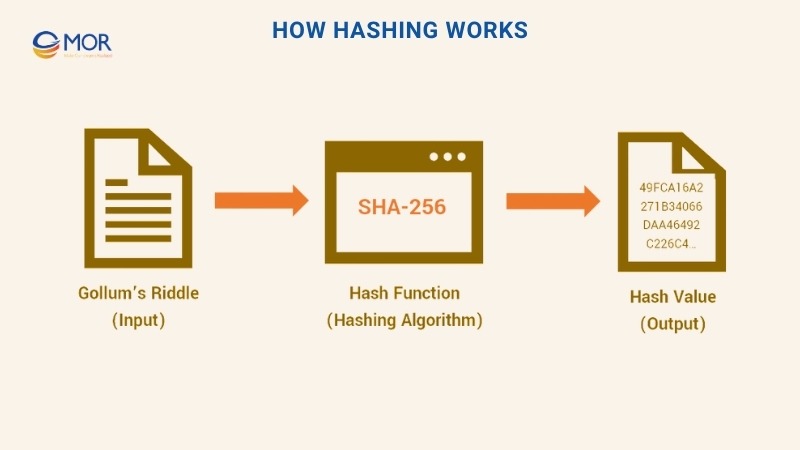
Now that you understand the idea behind these methods, let us look at how they work in practice. A hash function example in cryptography helps show how different inputs produce fixed-size outputs. Imagine you take this riddle from The Hobbit and use it as your input:
“It cannot be seen, cannot be felt,
Cannot be heard, cannot be smelt.
It lies behind stars and under hills,
And empty holes it fills.
It comes out first and follows after,
Ends life, kills laughter.”
We will not reveal the answer here, but if you pass this riddle through a SHA-256 method, you get an output that looks like this:
49FCA16A2271B34066DAA46492C226C4D4F61D56452A1E1A01A3201B234509A2
The picture below shows the steps that turn the riddle into its final digest.
What if you try a much shorter input instead? For example, “The Lord of the Rings.” The output still has the same size, as shown here:
01912B8E8425CFF006F430C15DBC4991F1799401F7B6BEB0633E56529FE148B9
Both results are 256 bits long and display as 64 hexadecimal characters. No matter how long or short your text is, using the same method creates an output of the same length. This steady behavior comes from the deterministic design of the method.
If you take the original riddle and run it through MD5 instead, you get a much shorter value:
B53CE8A3139752B10AAE878A15216598
This difference happens because MD5 creates 32 hexadecimal characters. That is half the size of SHA-256. Even so, every MD5 result has the same fixed length, no matter the input.
If you choose SHA-512 for the same riddle, you see the opposite effect. This method produces a much longer result, like this one:
6DC1AAE5D80E8F72E5AF3E88A5C0FA8A71604739D4C0618182303EEEB1F02A0DBA319987D5B5F717E771B9DA1EAD7F3F92DC8BA48C064D41DD790D69D7D98B44
Different methods create different lengths, but each one stays consistent for every input it receives.
Hash Function Vs Encryption In Cryptography
People often ask if hashing and encryption are the same thing. The answer is no. Both use algorithms inside security systems, but that is where the similarity ends. They serve different goals and work in different ways.
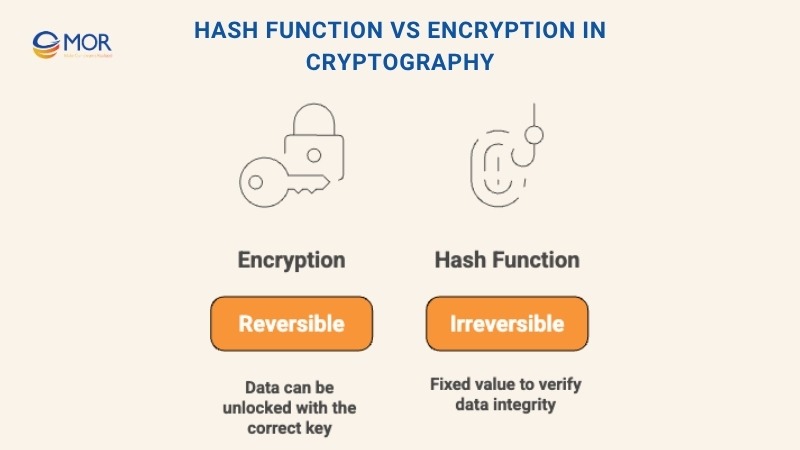
A hash function in cryptography is a one-way process. It turns readable data into an unreadable string, and there is no method to turn that string back into the original message. The goal is to create a fixed value that helps with checking data and keeping it safe from changes.
Encryption works as a two-way process. It hides data so only the correct person with the right key can open it again. You lock the data with encryption, and someone with permission can unlock it later. This difference is what separates hashing from encryption in everyday digital systems.
Examples Of Common Hash Algorithms And Families Of Algorithms
Now that you understand how these methods work, let us look at the families that appear most often in secure systems. Many standards, including NIST guidelines, describe how these methods should be used. One well known option today is the sha256 cryptographic hash function, which is part of a larger group of designs.
Here are some common families:
- Secure Hash Algorithm (SHA). This group includes SHA-1, the SHA-2 family (SHA-224, SHA-256, SHA-384, SHA-512), and SHA-3 versions. SHA-1 is no longer safe. Today, SHA-256 is one of the most widely used methods in modern systems.
- Message Digest (MD). This family includes MD2, MD4, MD5, and MD6. MD5 was once very popular, but it is now considered unsafe because it can create collisions in real situations.
- Windows NTHash. Also called a Unicode or NTLM hash, this method is common on Windows devices. It is safer than the older LM hash, but NTLM still has known weaknesses. NTLMv1 is rarely used now, while NTLMv2 is still active in many systems.
Other well known designs include BLAKE2, BLAKE3, RIPEMD-160, and WHIRLPOOL. They support many platforms and continue to play a role in modern security tasks.
Keytakeaway Of Hash Function In Cryptography (Tl;Dr)
There is a lot to understand about hashing. You have learned what these methods are, how they work, and where they appear in everyday systems and tools.
- Hashing helps with indexing and finding items in large datasets. It also helps check data for any hidden changes.
- In security, hashing takes readable input and uses a math process to create a fixed-length value.
- A hash function in cryptography is deterministic. This means the output size is always the same, no matter how long the input is. It is also resistant to collisions and preimage attacks.
- Collision resistance means two different inputs should never create the same result.
- Preimage resistance means the process cannot be reversed to find the original message, so it is treated as a one-way path.
- Any small change in the input creates a completely new value. This strong reaction is known as the avalanche effect.
- Different methods exist, each with different speeds and sizes. For example, SHA-256 creates a 256-bit result, shown as 64 characters in hexadecimal form.
These ideas show why hashing is a key part of many secure systems today.
How MOR Software Uses Hash Functions For Secure Development
At MOR Software, security is part of every solution we build. We use hash function in cryptography methods to protect user data, confirm identity, and keep information unchanged during transmission. In fields like healthcare and finance, hashing helps secure medical records, financial details, and login credentials from unwanted access.
Our engineers apply hashing inside Salesforce systems, mobile apps, and large enterprise platforms. It supports user authentication and protects communication between services. In the Workforce Management System with Salesforce and Slack Integration, hashed credentials help keep access safe and data flow steady.
We also follow global standards like ISO 9001:2015 and ISO/IEC 27001:2013. Our team combines strong algorithms with trusted frameworks to stop breaches and maintain confidence. With ongoing improvements, MOR Software continues to strengthen its security practice and deliver smart, scalable solutions that protect data for the long run.
Conclusion
A hash function in cryptography gives your systems a simple, reliable way to protect data, verify changes, and keep sensitive information safe. Understanding how it works helps teams choose the right method for each task, from user authentication to secure communication. MOR Software builds solutions with strong hashing practices at the core. If you want secure, scalable, and future ready technology for your next project, contact us and our experts will support you.
Rate this article
0
over 5.0 based on 0 reviews
Your rating on this news:
Name
*Email
*Write your comment
*Send your comment
1